部署 dashboard
根據官方文的安裝介紹,直接遠程執行即可,這里先下載下來,然后執行:
[root@master ~]# wget https://raw.githubusercontent.com/kubernetes/dashboard/v1.10.1/src/deploy/recommended/kubernetes-dashboard.yaml
[root@master ~]# kubectl apply -f kubernetes-dashboard.yaml
secret/kubernetes-dashboard-certs created
serviceaccount/kubernetes-dashboard created
role.rbac.authorization.k8s.io/kubernetes-dashboard-minimal created
rolebinding.rbac.authorization.k8s.io/kubernetes-dashboard-minimal created
deployment.apps/kubernetes-dashboard created
service/kubernetes-dashboard created
查看
[root@master ~]# kubectl get pods -n kube-system
NAME READY STATUS RESTARTS AGE
coredns-5c98db65d4-8mzfz 1/1 Running 0 44d
coredns-5c98db65d4-spjx8 1/1 Running 0 44d
etcd-master.kubernetes 1/1 Running 0 44d
kube-apiserver-master.kubernetes 1/1 Running 0 44d
kube-controller-manager-master.kubernetes 1/1 Running 0 44d
kube-flannel-ds-amd64-4szk7 1/1 Running 0 44d
kube-flannel-ds-amd64-b4ssp 1/1 Running 1 44d
kube-flannel-ds-amd64-nmklz 1/1 Running 0 44d
kube-flannel-ds-amd64-wjczq 1/1 Running 0 44d
kube-proxy-8fqsz 1/1 Running 0 44d
kube-proxy-bkrw4 1/1 Running 0 44d
kube-proxy-n75g8 1/1 Running 1 44d
kube-proxy-rmckk 1/1 Running 0 44d
kube-scheduler-master.kubernetes 1/1 Running 0 44d
kubernetes-dashboard-7d75c474bb-cqwh6 1/1 Running 0 18s # 已經啟動成功
開放訪問
默認dashboard中啟動的svc只能集群內部訪問,所以需要手動配置對外訪問,打一個補丁即可:
[root@master ~]# kubectl patch svc kubernetes-dashboard -p '{"spec":{"type":"NodePort"}}' -n kube-system
service/kubernetes-dashboard patched
[root@master ~]# kubectl get svc -n kube-system
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
kube-dns ClusterIP 10.96.0.10 <none> 53/UDP,53/TCP,9153/TCP 44d
kubernetes-dashboard NodePort 10.106.202.90 <none> 443:30090/TCP 3m16s
通過查看,dashboard的svc已經被映射到30090 這個端口,所以在瀏覽器直接輸入任意節點的ip + 端口即可訪問。
注意訪問的地址是 https://IP:PORT
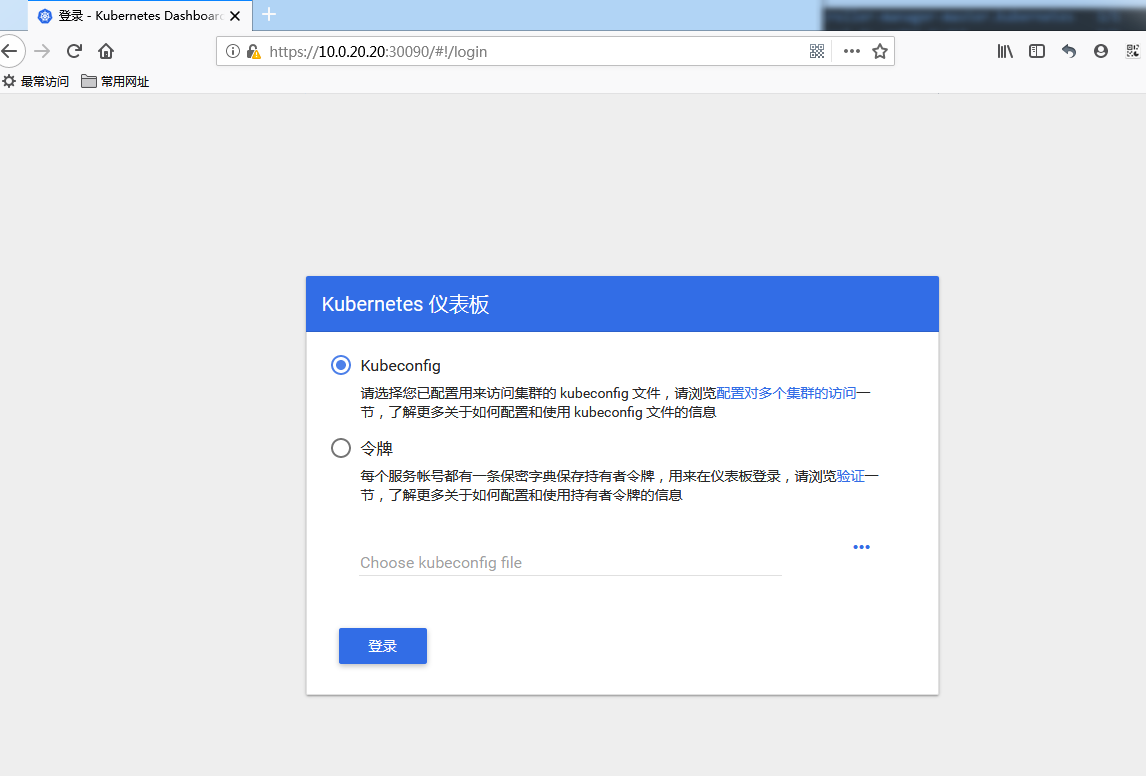
配置dashboard用戶
Dashboard 登陸有兩種認證方式:
- kubeconfig 文件認證
- token 令牌認證
下面對這兩種認證都進行測試驗證
1. token 令牌認證
創建一個 serviceAccount
在 kube-system 名稱空間中創建
[root@master ~]# kubectl create serviceaccount dashboard-admin -n kube-system
[root@master ~]# kubectl describe sa/dashboard-admin -n kube-system
Name: dashboard-admin
Namespace: kube-system
Labels: <none>
Annotations: <none>
Image pull secrets: <none>
Mountable secrets: dashboard-admin-token-wrdvz
Tokens: dashboard-admin-token-wrdvz
Events: <none>
dashboard-admin 綁定 clusterbinding 的 sa
[root@master ~]# kubectl create clusterrolebinding dashboard-cluster-admin --clusterrole=cluster-admin --serviceaccount=kube-system:\dashboard-admin
clusterrolebinding.rbac.authorization.k8s.io/dashboard-cluster-admin created
[root@master ~]# kubectl describe clusterrolebinding/dashboard-cluster-admin
Name: dashboard-cluster-admin
Labels: <none>
Annotations: <none>
Role:
Kind: ClusterRole
Name: cluster-admin
Subjects:
Kind Name Namespace
---- ---- ---------
ServiceAccount dashboard-admin kube-system
這幫綁定后,serviceaccount 的 dashboard-admin 就有集群的管理員權限了。
獲取 serviceaccount 的 dashboard-admin 的secret信息
在創建好serviceaccount 的 dashboard-admin 后,會在 kube-system名稱空間下的secret 中,自動創建一個 以 dashboard-admin 開頭的 secret,攜帶者 token 字樣
[root@master ~]# kubectl get secret -n kube-system
NAME TYPE DATA AGE
attachdetach-controller-token-7nxx6 kubernetes.io/service-account-token 3 44d
bootstrap-signer-token-c44r9 kubernetes.io/service-account-token 3 44d
bootstrap-token-cgw8vp bootstrap.kubernetes.io/token 7 44d
certificate-controller-token-6682d kubernetes.io/service-account-token 3 44d
clusterrole-aggregation-controller-token-g7l5s kubernetes.io/service-account-token 3 44d
coredns-token-gsrxq kubernetes.io/service-account-token 3 44d
cronjob-controller-token-qch7l kubernetes.io/service-account-token 3 44d
daemon-set-controller-token-gmp2z kubernetes.io/service-account-token 3 44d
# 下面這個就是自動生成的
dashboard-admin-token-wrdvz kubernetes.io/service-account-token 3 6m50s
default-token-ll59x kubernetes.io/service-account-token 3 44d
... ...
... ...
從上已經查看到了,下面需要查看一下詳細信息即可獲取到token的值
[root@master ~]# kubectl describe secret/dashboard-admin-token-wrdvz -n kube-system
Name: dashboard-admin-token-wrdvz
Namespace: kube-system
Labels: <none>
Annotations: kubernetes.io/service-account.name: dashboard-admin
kubernetes.io/service-account.uid: 4c593334-7f68-4190-85a2-f92fcab234d4
Type: kubernetes.io/service-account-token
Data
====
namespace: 11 bytes
token: eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlLXN5c3RlbSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJkYXNoYm9hcmQtYWRtaW4tdG9rZW4td3JkdnoiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC5uYW1lIjoiZGFzaGJvYXJkLWFkbWluIiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQudWlkIjoiNGM1OTMzMzQtN2Y2OC00MTkwLTg1YTItZjkyZmNhYjIzNGQ0Iiwic3ViIjoic3lzdGVtOnNlcnZpY2VhY2NvdW50Omt1YmUtc3lzdGVtOmRhc2hib2FyZC1hZG1pbiJ9.YxE09BRCQbUA_nzE60s9eXOYZMjsWLEZfXqXuiRffpsl_KgfosSKtII_YbBESvLeaSi3qivrkgSNKHdPytS2zmZd9BdNbGbABjecRER5jSjNNeRjok6cixghSVR51VyzJN5PlpPHtlhOlshJLXg_IAXtYzq36AZTf4LQ5_17k_1DXIjOsL5j0N0CEljcQVvOhEPlyu3OGsVEJOijKSMcEXJmrV2z5Z4rUczSn83qNy1ZjT-DF2Avg3eMua5Pw0LkgP9zQF76q2MGYwWZDc5z0y53SoYxs7k12OKnRrHL0Vai11a8snGLH_Dt7jXY0UAKwpew6a6Gj4F4xsK1InxBtg
ca.crt: 1025 bytes
上面查看到的token 后面的一大串就是,把這一串復制到頁面中就可以登錄。

2. kubeconfig 文件認證
創建測試一個權限小一點的,只能訪問default名稱空間資源的賬戶
創建一個 serviceAccount
[root@master pki]# kubectl create serviceaccount def-ns-admin -n default
serviceaccount/def-ns-admin created
[root@master pki]# kubectl describe sa/def-ns-admin -n default
Name: def-ns-admin
Namespace: default
Labels: <none>
Annotations: <none>
Image pull secrets: <none>
Mountable secrets: def-ns-admin-token-qfrqj
Tokens: def-ns-admin-token-qfrqj
Events: <none>
創建 rolebinding 綁定 def-ns-admin
[root@master pki]# kubectl create rolebinding def-ns-admin --clusterrole=admin --serviceaccount=default:def-ns-admin
rolebinding.rbac.authorization.k8s.io/def-ns-admin created
[root@master pki]# kubectl describe rolebinding/def-ns-admin -n default
Name: def-ns-admin
Labels: <none>
Annotations: <none>
Role:
Kind: ClusterRole
Name: admin
Subjects:
Kind Name Namespace
---- ---- ---------
ServiceAccount def-ns-admin default
提示:這里和上面一樣,到此步驟系統已經自動創建出一個secret,詳細信息中包含token,可以直接使用此token登錄dashboard,只能管理default名稱空間下的資源。
創建集群和創建kubeconfig配置文件
[root@master pki]#
[root@master pki]# kubectl config set-cluster kubernetes --certificate-authority=./ca.crt --server="https://10.0.20.20:6443" --embed-certs=true --kubeconfig=/root/def-ns-admin.conf
Cluster "kubernetes" set.
[root@master pki]# kubectl config view --kubeconfig=/root/def-ns-admin.conf
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: DATA+OMITTED
server: https://10.0.20.20:6443
name: kubernetes
contexts: []
current-context: ""
kind: Config
preferences: {}
users: []
拿到 def-ns-admin 用戶的base64格式的token
先拿到對應的token后base64 解碼
[root@master pki]# kubectl get secret def-ns-admin-token-qfrqj -o jsonpath={.data.token} | base64 -d
eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJkZWZhdWx0Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZWNyZXQubmFtZSI6ImRlZi1ucy1hZG1pbi10b2tlbi1xZnJxaiIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJkZWYtbnMtYWRtaW4iLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC51aWQiOiI2ZGU3NWU2Mi1hYjViLTQyMWItOTJhYS0zN2IyMjRmODBmNjEiLCJzdWIiOiJzeXN0ZW06c2VydmljZWFjY291bnQ6ZGVmYXVsdDpkZWYtbnMtYWRtaW4ifQ.k7Oq2V93mz60qxP8Xb2zOoJ9GwnlGbQjeYLJqfqTp-tuhThi_s542GpPWYvEdha-kuxYuyxRf_MUEg-YBCmilS0mqQBVoiHdvJCH6kQTbdZCpJOlML5jXHX9py7TJr8grFHI1aoyo5ZXDM8yZ9tULCpVNLVRz6sCh2wHcCP-pNIA2eaiM_3xM6Ow-0igYe2lxsv2pZcMUWNdi-ImZ9Vv72Nb9sn9rzp2de9RbZ7KMnokihMCdx8pWw18OTNxG2cMTRJc2dMBRlFEgafMVwYnIKdoDemgbHnnRh7kF0p577lv_I-qpnV4ADO0j31nlm0iKS5VZ7i0PHkeg1KVMRDNmg
這樣就獲取到解碼后的值了,然后保存到變量中
[root@master pki]# DEF_NS_ADMIN_TOKEN=$(kubectl get secret def-ns-admin-token-qfrqj -o jsonpath={.data.token} | base64 -d)
這樣執行后就保存下來了
設置 set-credentials 保存至 def-ns-admin.conf
[root@master pki]# kubectl config set-credentials def-ns-admin --token=${DEF_NS_ADMIN_TOKEN} --kubeconfig=/root/def-ns-admin.conf
[root@master pki]# kubectl config view --kubeconfig=/root/def-ns-admin.conf
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: DATA+OMITTED
server: https://10.0.20.20:6443
name: kubernetes
contexts: []
current-context: ""
kind: Config
preferences: {}
users:
- name: def-ns-admin # 認證的serviceaccount
user:
token: eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJkZWZhdWx0Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZWNyZXQubmFtZSI6ImRlZi1ucy1hZG1pbi10b2tlbi1xZnJxaiIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJkZWYtbnMtYWRtaW4iLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC51aWQiOiI2ZGU3NWU2Mi1hYjViLTQyMWItOTJhYS0zN2IyMjRmODBmNjEiLCJzdWIiOiJzeXN0ZW06c2VydmljZWFjY291bnQ6ZGVmYXVsdDpkZWYtbnMtYWRtaW4ifQ.k7Oq2V93mz60qxP8Xb2zOoJ9GwnlGbQjeYLJqfqTp-tuhThi_s542GpPWYvEdha-kuxYuyxRf_MUEg-YBCmilS0mqQBVoiHdvJCH6kQTbdZCpJOlML5jXHX9py7TJr8grFHI1aoyo5ZXDM8yZ9tULCpVNLVRz6sCh2wHcCP-pNIA2eaiM_3xM6Ow-0igYe2lxsv2pZcMUWNdi-ImZ9Vv72Nb9sn9rzp2de9RbZ7KMnokihMCdx8pWw18OTNxG2cMTRJc2dMBRlFEgafMVwYnIKdoDemgbHnnRh7kF0p577lv_I-qpnV4ADO0j31nlm0iKS5VZ7i0PHkeg1KVMRDNmg
配置成功
配置 def-ns-admin.conf 上下文
[root@master pki]# kubectl config set-context def-ns-admin@kubernetes --cluster=kubernetes --user=def-ns-admin --kubeconfig=/root/def-ns-admin.conf
Context "def-ns-admin@kubernetes" created.
[root@master pki]# kubectl config view --kubeconfig=/root/def-ns-admin.conf
apiVersion: v1
clusters:
- cluster: # 這里是上面創建的集群
certificate-authority-data: DATA+OMITTED
server: https://10.0.20.20:6443 # 這里是集群地址
name: kubernetes # 這里集群名稱
contexts:
- context: # 上面創建的上下文
cluster: kubernetes # 集群
user: def-ns-admin # serviceaccount
name: def-ns-admin@kubernetes
current-context: "" # 這里還沒有配置當前上下文
kind: Config
preferences: {}
users:
- name: def-ns-admin
user:
token: eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJkZWZhdWx0Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZWNyZXQubmFtZSI6ImRlZi1ucy1hZG1pbi10b2tlbi1xZnJxaiIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJkZWYtbnMtYWRtaW4iLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC51aWQiOiI2ZGU3NWU2Mi1hYjViLTQyMWItOTJhYS0zN2IyMjRmODBmNjEiLCJzdWIiOiJzeXN0ZW06c2VydmljZWFjY291bnQ6ZGVmYXVsdDpkZWYtbnMtYWRtaW4ifQ.k7Oq2V93mz60qxP8Xb2zOoJ9GwnlGbQjeYLJqfqTp-tuhThi_s542GpPWYvEdha-kuxYuyxRf_MUEg-YBCmilS0mqQBVoiHdvJCH6kQTbdZCpJOlML5jXHX9py7TJr8grFHI1aoyo5ZXDM8yZ9tULCpVNLVRz6sCh2wHcCP-pNIA2eaiM_3xM6Ow-0igYe2lxsv2pZcMUWNdi-ImZ9Vv72Nb9sn9rzp2de9RbZ7KMnokihMCdx8pWw18OTNxG2cMTRJc2dMBRlFEgafMVwYnIKdoDemgbHnnRh7kF0p577lv_I-qpnV4ADO0j31nlm0iKS5VZ7i0PHkeg1KVMRDNmg
配置當前上下文
[root@master pki]# kubectl config view --kubeconfig=/root/def-ns-admin.conf
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: DATA+OMITTED
server: https://10.0.20.20:6443
name: kubernetes
contexts:
- context:
cluster: kubernetes
user: def-ns-admin
name: def-ns-admin@kubernetes
current-context: def-ns-admin@kubernetes # 當前上下文用戶
kind: Config
preferences: {}
users:
- name: def-ns-admin
user:
token: eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJkZWZhdWx0Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZWNyZXQubmFtZSI6ImRlZi1ucy1hZG1pbi10b2tlbi1xZnJxaiIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJkZWYtbnMtYWRtaW4iLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC51aWQiOiI2ZGU3NWU2Mi1hYjViLTQyMWItOTJhYS0zN2IyMjRmODBmNjEiLCJzdWIiOiJzeXN0ZW06c2VydmljZWFjY291bnQ6ZGVmYXVsdDpkZWYtbnMtYWRtaW4ifQ.k7Oq2V93mz60qxP8Xb2zOoJ9GwnlGbQjeYLJqfqTp-tuhThi_s542GpPWYvEdha-kuxYuyxRf_MUEg-YBCmilS0mqQBVoiHdvJCH6kQTbdZCpJOlML5jXHX9py7TJr8grFHI1aoyo5ZXDM8yZ9tULCpVNLVRz6sCh2wHcCP-pNIA2eaiM_3xM6Ow-0igYe2lxsv2pZcMUWNdi-ImZ9Vv72Nb9sn9rzp2de9RbZ7KMnokihMCdx8pWw18OTNxG2cMTRJc2dMBRlFEgafMVwYnIKdoDemgbHnnRh7kF0p577lv_I-qpnV4ADO0j31nlm0iKS5VZ7i0PHkeg1KVMRDNmg
這樣,就把當前 上下文的用戶配置成功
測試使用kubeconfig文件登陸
下載剛剛生成好的 def-ns-admin.conf
然后測試登陸:
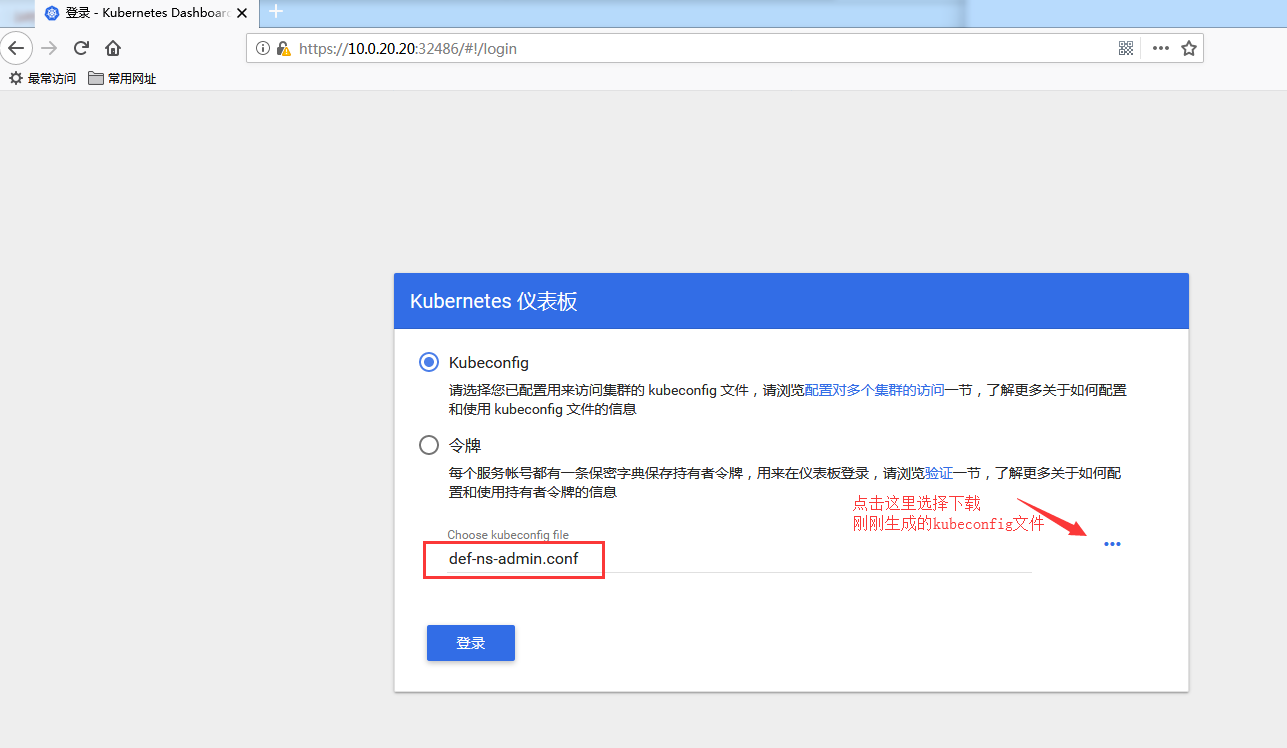

基於 tls 驗證
創建 dashboard 專用的 tls 證書
進入到 kubernetes 集群的 master 節點中的 /etc/kubernetes/pki/ 目錄
這個目錄是專門存放 kubernetes 集群證書的目錄
生成dashboard 用戶的私鑰
[root@master ~]# cd /etc/kubernetes/pki/
[root@master pki]# (umask 077; openssl genrsa -out dashboard.key 2048)
Generating RSA private key, 2048 bit long modulus
........................+++
.........................................................+++
e is 65537 (0x10001)
[root@master pki]# ll dashboard.key
-rw------- 1 root root 1679 Aug 22 17:51 dashboard.key
生成證書簽署請求
[root@master pki]# openssl req -new -key dashboard.key -out dashboard.csr -subj "/O=tracy/CN=dashboard"
[root@master pki]# ll dashboard.csr
-rw-r--r-- 1 root root 911 Aug 22 17:54 dashboard.csr
給dashboard證書簽證
這里需要注意,一定要kubernetes集群中的 ca.crt 和 ca.key 來簽署,這樣才能在此集群中使用。
[root@master pki]# openssl x509 -req -in dashboard.csr -CA ca.crt -CAkey ca.key -CAcreateserial -out dashboard.crt -days 365
Signature ok
subject=/O=tracy/CN=dashboard
Getting CA Private Key
這樣就簽署完成了
創建 dashboard 對應的 secret
[root@master pki]# kubectl create secret generic dashboard-cert -n kube-system --from-file=dashboard.crt --from-file=dashboard.key
secret/dashboard-cert created
[root@master pki]# kubectl get secret -n kube-system dashboard-cert
NAME TYPE DATA AGE
dashboard-cert Opaque 2 16s
[root@master pki]# kubectl describe secret -n kube-system dashboard-cert
Name: dashboard-cert
Namespace: kube-system
Labels: <none>
Annotations: <none>
Type: Opaque
Data
====
dashboard.crt: 1001 bytes
dashboard.key: 1679 bytes
